Hello World, I just let Sony stuff pass for a day and Boom. So much news! I just finished reading Brian Krebs' writings and man, he is a busy one. So is "Freedom to Tinker" There are a bunch of must read articles. Brian is a google news featured guy! Thanks Brian. Then there is an Owl who muttered about me! Thanks Owlish!
now to Sony Saga, there seems to be a bunch of security flaws introduced by This bad bad rootkit. I see them Here,here here here...
What ever you do the Sony Uninstaller Hole seem to Stay Open.
According to Felten (whose research was informed by a discovery from a Finnish researcher known as "Muzzy"), "the root of the problem is a serious design flaw in SonyÂ’s web-based uninstaller. When you first fill out Sony'’s form to request a copy of the uninstaller, the request form downloads and installs a program -- an ActiveX control created by the [digital rights management software] vendor, First4Internet -- called CodeSupport.
"CodeSupport remains on your system after you leave SonyÂ’s site, and it is marked as safe for scripting, so any Web page can ask CodeSupport to do things. One thing CodeSupport can be told to do is download and install code from an Internet site.
"Unfortunately, CodeSupport doesnÂ’t verify that the downloaded code actually came from Sony or First4Internet. This means any web page can make CodeSupport download and install code from any URL without asking the userÂ’s permission."
Another researcher, Kaminsky has done more work, Kaminsky said he's not sure yet how many individual computers inside of those 560,000 networks actually have the Sony software installed on them, but noted that "at the end of the day, it only takes an average of two machines per network and we are easily talking about millions of machines here."
His simple explanation on his Plotting is;
Sony has a rootkit.
The rootkit phones home.
Phoning home requires a DNS query.
DNS queries are cached.
Caches are externally testable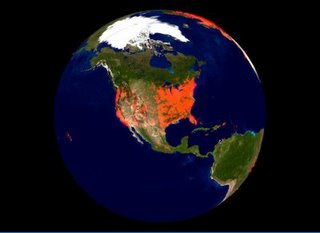
Viola! A Map.
Kaminsky tied the addresses to geographic locations by using his access to a commercial geolocation database. He has since posted a software tool on his site that renders a very cool three-dimensional look at where the largest concentrations of installs are located
I could go on, But I think you have a bunch to read for now.
Have a good day!
Wednesday, November 16, 2005
A train of Sony Flaws and an Owl Hoots!
Subscribe to:
Post Comments (Atom)
No comments:
Post a Comment